The Intelligence Layer for Secuity operations.
Unify Your Tools. Augment Your Team. Win the Fight.
Every vendor speaks a different language. Triad enforces canonical contracts so your data is consistent, queryable, and trusted across tenants.
Workflow-first orchestration replaces brittle scripts and ad-hoc triage with governed, auditable execution.
Your environment becomes a living graph of assets, identities, permissions, and evidence that drives correlation and prioritization.
Fufilling the promise, A True Single Pane of Glass.
A vendor-agnostic control plane, built on canonical contracts
Triad connects to your stack through a plugin runtime, normalizes raw vendor data into canonical objects, and enforces schema versions at the boundary. That gives you stable, consistent data shapes for every workflow, hunt, and report.

Deterministic operations.
Governed execution at scale.
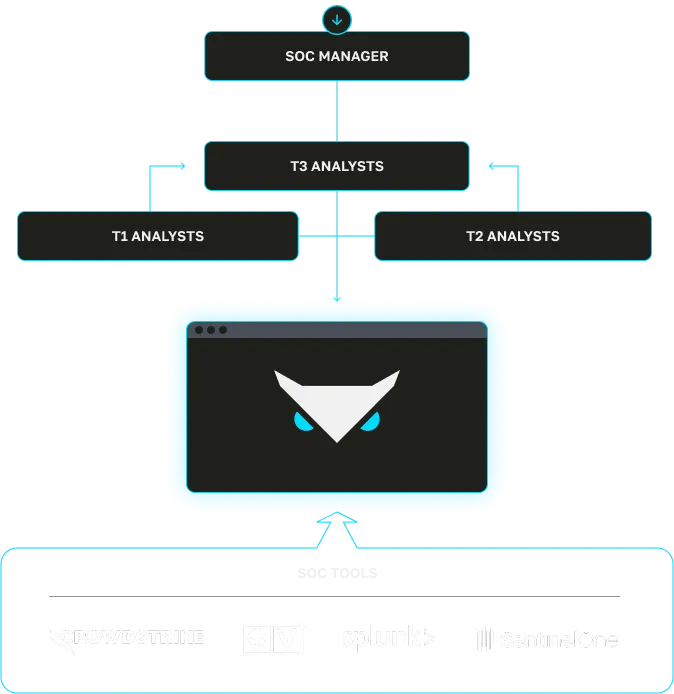
Triad Secure's workflow Layer: triggers, conditions, automation, human steps, and auditability. Tenant-scoped policies let MSSPs and enterprises apply consistent logic without forcing vendor standardization.
time
Cuts ticket handling time by 50% with unified search and intelligent automation.
ACCURACY
Triad Secure empowers security teams to make faster, more precise decisions by eliminating tool fragmentation and manual correlation.
Intelligence graph + attack path reasoning:
Compute what is actually exploitable
Triad models assets, identities, permissions, and evidence as a living graph across all vendors and tenants.
Attack path analysis: We compute viable paths using real permissions, reachability, and constraints (MFA, boundaries, telemetry), then surface the shortest fix sets that collapse the most risk.
Alert-scoped intelligence: Every alert slices the global graph to show blast radius, reachable objectives, and remediation priorities in seconds, not hours of manual correlation.
Hunt at scale: Canonical hunt definitions translate into vendor-native queries and return normalized evidence, so hunting becomes governed, repeatable, and measurable.
Objective-driven CNAPP delievers outcomes, not rules.
Triad Secure's multi-tenant intelligence layer models environments as a computable graph, then optimizes remediation against attacker objectives with provable paths and measurable impact.
Risk is goal-driven
- 8 attacker objectives, weighted by tenant impact
- Evidence-backed confidence chains, not heuristics
- Dominance rules prevent double-counting
Optimize what to fix
- Simulate remediation impact on attack paths
- Greedy submodular optimization with effort estimates
- Time-to-deny curves and diminishing returns
Millisecond context
- Global graph snapshot (Neo4j)
- Precomputed reachability and choke-point indexes
- Alert-scoped slicing with aggressive caching
Exploitability scoring
Triad scores exploitability using conditions, observability, and boundary constraints. This moves risk from theoretical to evidence-based.
exploitability = boundary_penalty * condition_penalty * observability_multiplier
- Transitive IAM chains across 5+ hops
- Explicit deny and boundary enforcement
- Usage evidence boosts confidence
From alert to action
Every alert receives objective context, blast radius, and prioritized fixes in seconds so analysts know what to do next and why it matters.
- Objective reachability per alert
- Smallest fix set that collapses risk
- Provable reasoning chains

Not just another case queue.
Triad orchestrates triage, enrichment, escalation, and response with governed, tenant-aware workflows that enforce how your SOC actually operates.
Queue orchestration and analyst collaboration.
Triad routes work automatically using workload-aware assignment, then enables real-time collaboration with native mentions and handoffs inside the platform.
Deterministic operations.
Measurable outcomes.
Canonical normalization + graph intelligence + governed workflows turn noisy stacks into repeatable operations: faster triage, lower costs, and zero vendor rip-and-replace.
FAQs
We’ve answered the most common questions from MSSPs and medium to large SOC teams to help you understand how Triad Secure can transform your operations.
A Veteran-Owned Start up
Triad Secure is an Arizona based company with an obsession for operational efficency and decades of experience in the Cybersecurity industry

Triad Secure was founded to solve the problems our team expienced first hand. Our team knows the struggles Security operation centers deal with on a daily basis, because we have been there. We knew there had to be a better way, so instead of waiting for the tool we needed, we built it. Systematically engineering solutions to all of the problems we faced.
Founded by military veterans Tyler Arnone and Jake Shirvinski, our team brings decades of cybersecurity experience spanning defense, critical infrastructure, and enterprise SOC operations. That background shaped Triad’s core doctrine: operational truth must be computable, deterministic, and vendor-agnostic.
We built Triad to help MSSPs and enterprises run security at scale: Natively multi-tenanted, heterogeneous stacks, and real-world constraints. The result is faster response, better prioritization, and measurable risk collapse without disrupting existing tools.